About SIMULIA Execution Engine Security | ||
| ||
The SIMULIA Execution Engine administrator can pick and choose which features to implement and can add features over time to improve the security of the system. It might be desirable to start with an open system for prototyping or proof-of-concept implementations and then apply more security features as the needs of your organization dictate. It is important for the SIMULIA Execution Engine administrator to read and understand the significance of each security feature to decide if it is appropriate for a specific environment.
Some aspects of SIMULIA Execution Engine security are provided by the native operating systems (such as file access security), some are provided by database and application server middleware, and some are built into the SIMULIA Execution Engine system itself. Some basic knowledge of all of these areas is necessary to make a determination of which features should be applied in a given environment. In addition, a basic understanding of the security tools provided by those systems is also essential to configure and deploy SIMULIA Execution Engine security features. This section provides step-by-step instructions for activating these security features, as well as a discussion of the systems involved, which will aid the SIMULIA Execution Engine administrator in determining the proper configuration for a specific computing environment.
Some security features described in this section interact with other SIMULIA Execution Engine features or have prerequisites. Such interactions and prerequisites are described in each section as appropriate.
About Database Security
Regardless of which SIMULIA Execution Engine security features are used, the SIMULIA Execution Engine database is always protected by the application server and database middleware layers.
This arrangement is shown in the figure below.
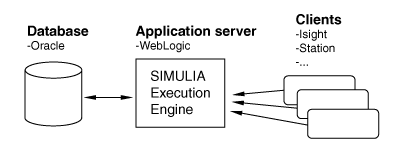
The only access to the database is via the WebLogic application server. The application server is configured with the proper credentials to access the database and maintains the only secure connection with the database. The database is not directly exposed to any SIMULIA Execution Engine user. Users cannot open JDBC or ODBC connections to the database unless the database administrator has allowed it. The SIMULIA Execution Engine does not support direct database connections, but it does not prevent them if the database administrator has given such access using tools outside of the SIMULIA Execution Engine.
![]()
About the Open (Non-secure) Configuration Option
The default installation of the SIMULIA Execution Engine provides an open environment. In this type of environment, no security is provided and user access is not controlled via user names and passwords.
Most other security features of the SIMULIA Execution Engine are disabled or ineffective in this mode. For example, although Access Control Lists can be defined, the control lists are not useful since all users share a single user ID. Furthermore, SIMULIA Execution Engine Federation (B2B) features will not function in this open configuration. This mode of operation is useful to verify correct operation of the system during a new installation or for prototyping and proof-of-concept environments.
The SIMULIA Execution Engine, however, requires that a security policy be defined in the WebLogic server. This action ensures that no user can gain access to the SIMULIA Execution Engine without first supplying credentials.
Administrators should be aware that any user that is authenticated by the SIMULIA Execution Engine server can perform any SIMULIA Execution Engine function on that server including running models, deleting job results, using the SIMULIA Execution Engine Dashboard to view lists of stations and running jobs, etc.